
0330 174 9900
info@espok.co.uk
Warlies Park House
Horseshoe Hill
Upshire, Essex
EN9 3SL
0330 174 9900
info@espok.co.uk
Warlies Park House
Horseshoe Hill
Upshire, Essex
EN9 3SL

0330 174 9900
info@espok.co.uk
Warlies Park House
Horseshoe Hill
Upshire, Essex
EN9 3SL
We employ the zero trust method to protect your organisation. Nothing is trusted unless it’s known to be protected with core security and principles to keep endpoints safe and secure.
The old way of security does not provide business agility, user experiences, and protections needed for a rapidly evolving digital estate. Many organizations are implementing Zero Trust to alleviate these challenges and enable the new normal of working anywhere, with anyone, at any time.
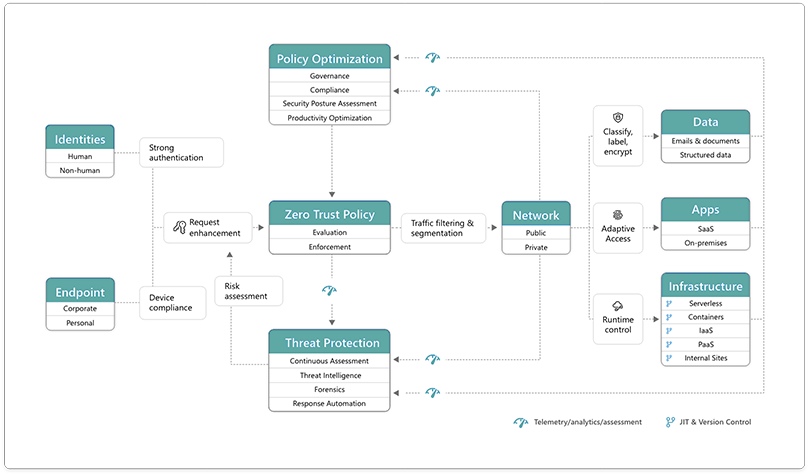
Zero Trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted or keeping access to applications and data. Zero Trust assumes that there is no traditional network edge; networks can be local, in the cloud, or a combination or hybrid with resources anywhere as well as workers in any location.
We’re truly at a unique time, with the ability to redefine work.
In this era of hybrid work, work is not where you go, it’s what you do and how you do it. Powered by the convergence of people, technology, and places, this shift has permanently reshaped expectations of employers and employees alike. To navigate this changing landscape, informed decision-making is needed now more than ever.
Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network. Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to “never trust, always verify.” Every access request is fully authenticated, authorized, and encrypted before granting access. Microsegmentation and least privileged access principles are applied to minimize lateral movement. Rich intelligence and analytics are utilized to detect and respond to anomalies in real time.


We can secure any platform with the endpoint tools we use, if you work exclusively with Microsoft or Google we can make sure your end points are protected on laptops, tablets and mobile devices.